Quantum computing is no longer science fiction. Labs worldwide are sprinting toward “Q-Day,” the moment a production-grade quantum computer can crack today’s encryption.
FS-ISAC has already set a 2035 deadline for migrating critical systems to post-quantum cryptography, calling the effort “a collaborative project,” not a race. Crypto exchanges—guarding more than US $3 trillion—feel the heat first.
We compared seven quantum-risk assessment tools, from free self-checks to deep-dive audits, so you can pinpoint weaknesses now and harden your platform before quantum hackers arrive.
Classical defenses collapse once Shor’s algorithm reaches production grade. Every Bitcoin or Ethereum transaction relies on ECDSA signatures; a cryptographically relevant quantum computer could forge those keys in minutes, draining wallets before an incident-response team can log in.
Attackers already understand the timeline. They are “harvesting encrypted data today, planning to decrypt it once quantum capabilities mature,” an ISACA bulletin warns (isaca.org). Stolen wallet backups, TLS captures, and cold-storage archives can sit in criminal vaults until Q-Day.
Project 11’s public Yellowpages dataset, which tracks quantum-exposed Bitcoin addresses, puts the number at roughly 6.3 million coins—about US $648 billion—as of January 17, 2025. That scale makes “harvest-now, decrypt-later” feel less hypothetical and more like a ticking countdown for any exchange holding customer keys.
Regulators feel the pressure. FS-ISAC’s 2025 roadmap tells financial institutions to complete their post-quantum migration by 2035 and calls the effort “a collaborative project,” not a contest (americanbanker.com). Exchanges courting institutional clients, or eyeing public listings, will face pointed questions about that roadmap.
The technical lift is heavy. An exchange runs hot wallets, custody HSMs, microservices, mobile apps, and smart-contract bridges. Each piece tucks cryptography into different corners of code, vendor APIs, or hardware modules. Inventorying that sprawl by hand borders on impossible.
That complexity is why purpose-built assessment tools matter. Automated scanners uncover hidden RSA certificates. Consulting teams map risk across governance, vendor chains, and supply paths. Continuous monitors flag any API that falls back to a weak cipher.
We need visibility before we can swap algorithms. The next sections break down seven solutions that give exchanges that X-ray view. Migration starts with facts, not guesses.
A good tool catches risk, while a great one fits the messy reality of an exchange. We built a scorecard that rewards both.
First, we weighted seven criteria that matter in daily crypto operations. Cryptographic coverage carries the most weight. If a scanner skips cold-wallet keys or on-chain signatures, everything else is moot.
Next comes integration ease. Exchanges move fast, so any solution that breaks CI pipelines or needs weeks of professional services drops on our chart. Regulatory alignment shares the spotlight, because boards want evidence they can hand to the SEC, an EU auditor, or a Big Four due-diligence team without extra Excel gymnastics.
We also score reporting depth, upgrade runway, vendor trust, and pricing flexibility. Together, these factors reveal whether a product can grow from a side-project proof of concept to a core control.
Each vendor earned a one-to-five score in every column. We multiplied by the weights, tallied the totals, then checked the math against real-world case studies. The top overall score claims spot #1, but every entrant met a minimum bar for credibility and quantum-risk relevance.
The result is a practical hierarchy. Use it to decide which tool to test first when time, budget, or engineering hours are tight.
On its homepage, the quantum cryptography firm says it is “securing digital assets for the post-quantum era.” Project Eleven makes one clear promise: lock down blockchain assets before quantum attackers can reach them.
The team lives and breathes crypto. Its methodology, detailed on Project 11 Post Quantum Cryptography, has engineers audit an exchange’s wallets, smart-contract bridges, and key-management back ends, flagging every place where ECDSA, RSA, or aging TLS still lurk. You receive a roadmap that ranks each weakness by business impact and points to fixes, often using their open-source Yellowpages toolkit to generate quantum-resistant keys without rewriting your entire stack.
Exchanges appreciate the hands-on style. Engagements finish in weeks, not quarters, and wrap with developer-ready pull requests plus board-level summaries. Because the firm focuses only on digital-asset security, recommendations already speak the language of custody layers, hot-wallet latency, and on-chain refactoring.
The trade-off is a shorter client list than legacy vendors. For teams that value speed, domain depth, and an immediate path to post-quantum cryptography, Project Eleven earns the top position in our ranking.
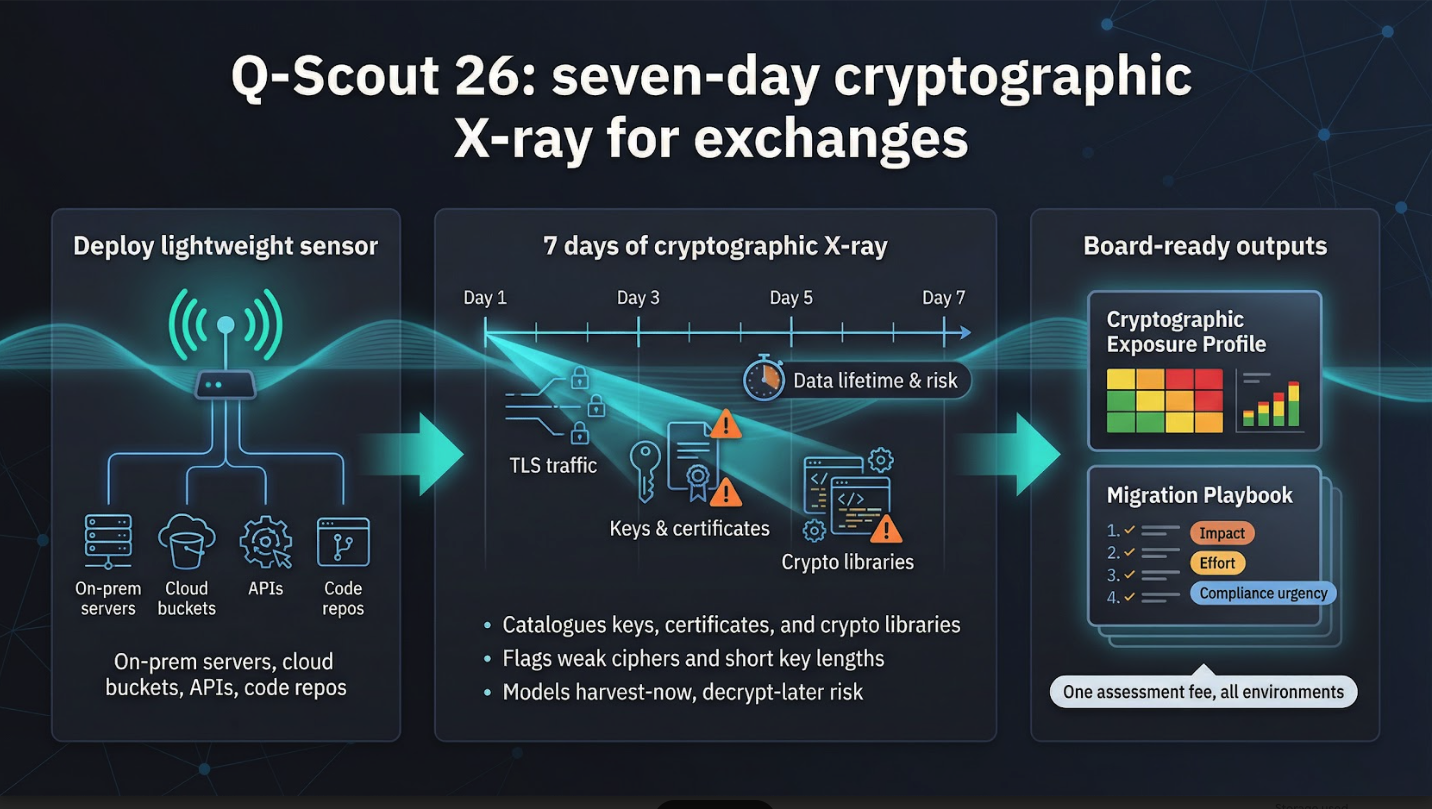
Some exchanges want answers yesterday. Q-Scout 26 is built for that urgency.
You deploy a lightweight sensor, point it at on-prem servers, cloud buckets, and third-party APIs, then let it run for a week. The platform catalogues every certificate, key, and cryptographic library it encounters, flags weak ciphers, and grades each system by how long its data must remain secret. In the exit call, you receive a crisp “Cryptographic Exposure Profile” plus a migration playbook ranked by impact, effort, and compliance urgency.
Speed does not equal superficial. Q-Scout inspects legacy code repositories as easily as live traffic captures. It also models “harvest-now, decrypt-later” scenarios, prompting teams to consider where today’s packet captures could surface tomorrow.
Pricing stays predictable: one assessment fee, no matter how sprawling your microservice map looks. Follow-on modules are available, but the initial deliverable already checks the boxes for most boards and regulators.
Security leaders use Q-Scout as a launchpad. It pinpoints the largest quantum risk gaps so developer hours land where they matter most.
Code reviews catch yesterday’s bugs, while CipherInsights watches tomorrow’s traffic.
You plug a passive sensor into your core switch or cloud mirror. From that vantage point, the platform inspects every packet, tagging weak TLS versions, expired certificates, and unencrypted service-to-service calls. Quantum Xchange tracks dozens of quantum-risk factors in near real time, giving security teams a clear view of gaps before attackers can act.
Continuous baselining is the advantage. Deploy a new microservice and, within minutes, the dashboard warns if its certificate chain still relies on RSA-2048 or SHA-1. That quick feedback shortens crypto-agility loops: developers patch once, auditors stop hunting.
Because CipherInsights operates at the network layer, it avoids language wars. Rust, Go, or Solidity—it only sees the handshake. For exchanges juggling on-prem, cloud, and vendor links, that neutrality turns confusion into clarity. You fix what is risky, ignore what is not, and move forward.
Some problems call for whiteboards, not Wi-Fi sniffers. evolutionQ brings seasoned cryptographers into workshops that unpack every dependency, supplier contract, and governance policy your exchange relies on.
The engagement feels closer to management consulting than pen testing. Over several weeks, analysts interview product owners, review architecture diagrams, and map data lifetimes against quantum-risk timelines. The final report reads like a board memo: a ranked risk register, budget estimates, and a migration sequence aligned with NIST’s post-quantum standards.
Depth is the differentiator. evolutionQ does more than say “upgrade TLS.” It pinpoints which customer segments, revenue streams, or regulatory filings break first if that certificate is harvested today and cracked later. Security roadmaps suddenly resonate with finance and legal teams, and real budget follows.
For exchanges planning an IPO or banking partnership, that strategic clarity often outweighs the slower turnaround and higher price tag. evolutionQ delivers the narrative executives need to green-light the engineering work.
Smart-contract code is its own dialect. ChainScore speaks it natively and adds a quantum layer.
During an engagement, auditors comb through Solidity or Rust repositories just as they hunt for re-entrancy bugs. This time they highlight public-key exposures, outdated signature libraries, and bridge logic that still assumes classical security. Code findings are paired with infrastructure scans, checking whether multi-sig wallets, MPC custody, and threshold schemes can shift to Dilithium or SPHINCS+ without hurting user experience.
The deliverable mirrors a classic audit report: severity ratings, line-number references, and remediation snippets. An appendix quantifies how many on-chain transactions would be forgeable if Shor’s algorithm arrived tomorrow and flags smart contracts that leak raw public keys into block data.
ChainScore is a boutique shop, so scheduling slots fill quickly and ongoing monitoring is not part of the package. For exchanges launching DeFi features or cross-chain bridges, however, this audit is the fastest route to quantum-risk assurance at the protocol layer.
Large exchanges run on sprawling microservice fleets. IBM Quantum Safe Explorer crawls each repository to map quantum risk at the code level.
Point the scanner at your Git repos or CI pipeline, and it builds a cryptographic bill of materials within a few hours. Hard-coded RSA keys in a forgotten admin tool, or deprecated ECDSA in the mobile app, surface in a sortable dashboard before your next sprint planning session.
Explorer pairs with Quantum Safe Advisor to block any pull request that reintroduces banned algorithms. That guardrail turns one-time cleanups into a permanent habit. The trade-off is setup heft: containerized analyzers, policy servers, and developer plug-ins require solid DevOps maturity and budget.
For exchanges with thousands of repositories and regulators on speed dial, the visibility return justifies the investment.
Not every exchange has budget for scanners, consultants, or full audits. Thales answers that gap with a free browser questionnaire that spots quantum risk blind spots in minutes.
The tool asks plain-English questions about key lengths, inventory processes, and post-quantum plans. Submit the form to receive a readiness score plus a bullet list of next steps. Treat it as a primer, not a prescription.
Because the results rely on self-reported data, the insight ceiling stays low. Even so, many security leads use the report as a conversation starter—a quick slide that proves quantum risk is on the roadmap and deserves real funding.
Need deeper coverage? Move up to one of the heavier tools above. Until then, Thales keeps the topic alive without stressing the travel budget.
A few patterns stand out.
Use these contrasts to match a tool mix to your own blind spots, culture, and timeline.
Start with honesty. List the assets you cannot afford to lose, the engineering hours you can dedicate this quarter, and the quantum risk tolerance your board will accept. That gap defines how aggressive your first move must be.
Early-stage exchange with ten engineers and a modest hot wallet? Run the Thales self-check tonight, then book a ChainScore audit when code freezes before launch.
Mid-size team juggling compliance questionnaires? Pair Q-Scout 26 for a fast, defensible inventory with CipherInsights for ongoing guardrails.
Regulated giant eyeing a public listing? Lean on evolutionQ for a governance narrative, IBM Explorer to keep developers honest, and Project Eleven for any wallet keys that live in cold storage.
Pick a starting point, secure the budget, and iterate. Quantum readiness is a program, not a purchase.